- Sort Score
- Result 10 results
- Languages All
Results 531 - 540 of 688 for Thread (0.04 sec)
-
fess-crawler/src/test/java/org/codelibs/fess/crawler/transformer/TransformerTest.java
// Transform operation ResponseData responseData = new ResponseData(); responseData.setUrl("http://thread" + threadId + ".com/page" + j); ResultData resultData = transformer.transform(responseData);Registered: Sun Sep 21 03:50:09 UTC 2025 - Last Modified: Sat Sep 06 04:15:37 UTC 2025 - 28K bytes - Viewed (0) -
android/guava/src/com/google/common/collect/ImmutableCollection.java
* appropriate factory method for details. View collections such as {@link * ImmutableMultiset#elementSet} iterate in the same order as the parent, except as noted. * <li><b>Thread safety.</b> It is safe to access this collection concurrently from multiple * threads. * <li><b>Integrity.</b> This type cannot be subclassed outside this package (which would allow * these guarantees to be violated). * </ul> *Registered: Fri Sep 05 12:43:10 UTC 2025 - Last Modified: Thu Aug 07 16:05:33 UTC 2025 - 21.4K bytes - Viewed (0) -
docs/recipes.md
``` ### Response Caching ([.kt][CacheResponseKotlin], [.java][CacheResponseJava]) To cache responses, you'll need a cache directory that you can read and write to, and a limit on the cache's size. The cache directory should be private, and untrusted applications should not be able to read its contents!
Registered: Fri Sep 05 11:42:10 UTC 2025 - Last Modified: Sat Aug 30 17:01:12 UTC 2025 - 47.8K bytes - Viewed (0) -
docs/bucket/replication/README.md
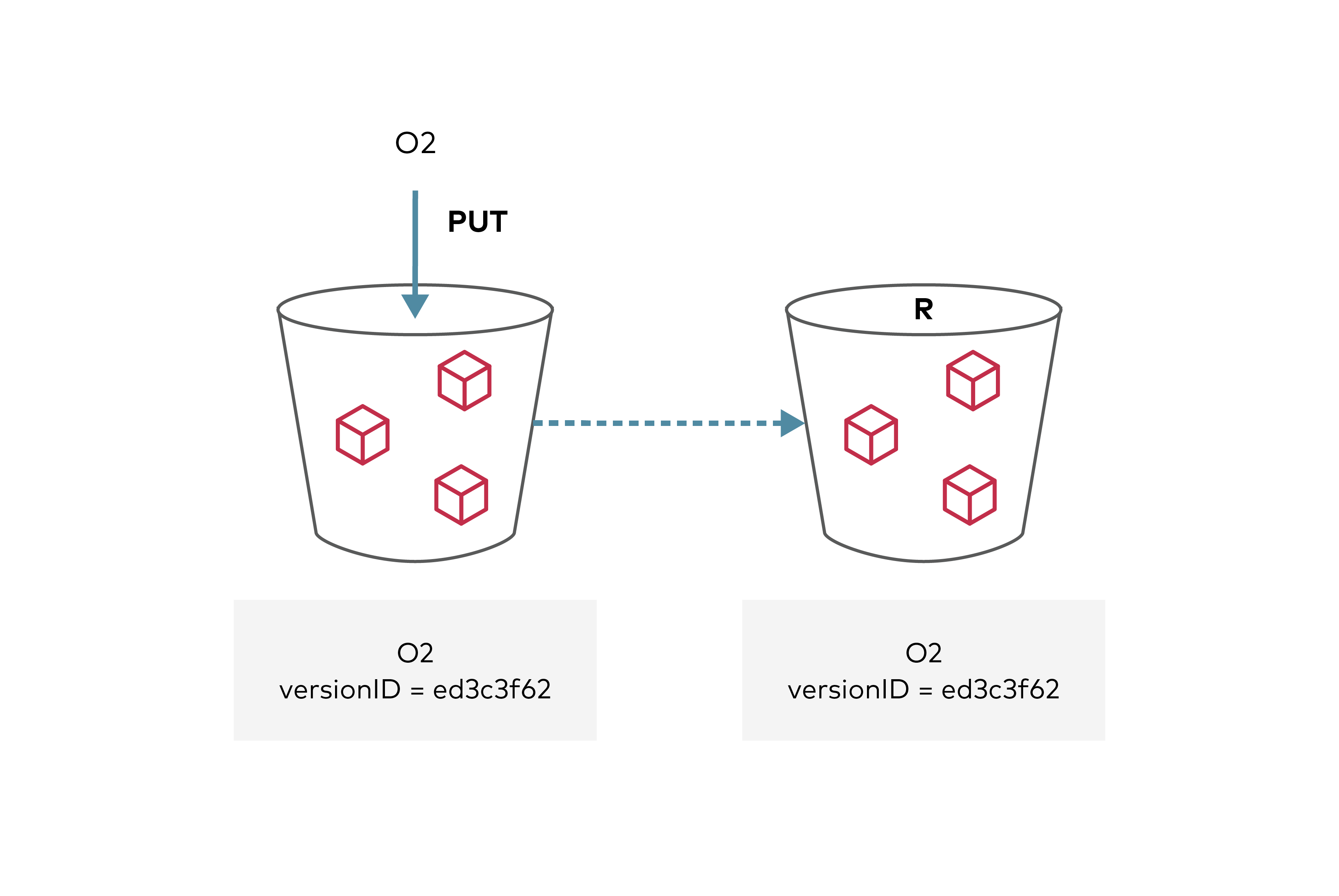 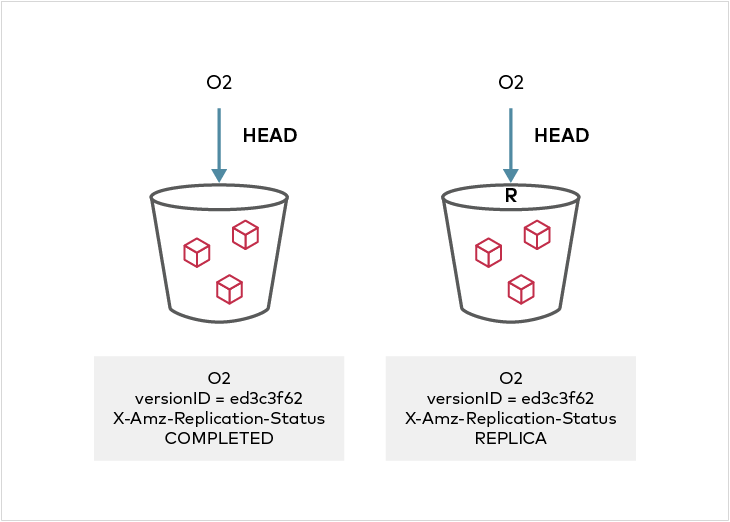 ## Replica Modification sync
Registered: Sun Sep 07 19:28:11 UTC 2025 - Last Modified: Tue Aug 12 18:20:36 UTC 2025 - 18.3K bytes - Viewed (0) -
fess-crawler/src/main/java/org/codelibs/fess/crawler/transformer/impl/XmlTransformer.java
* Retrieves an XPathAPI instance from the cache or creates a new one. * @return An XPathAPI instance. */ protected XPathAPI getXPathAPI() { try { return xpathAPICache.get(Thread.currentThread().getName()); } catch (final ExecutionException e) { if (logger.isDebugEnabled()) { logger.debug("Failed to retrieval a cache.", e); }Registered: Sun Sep 21 03:50:09 UTC 2025 - Last Modified: Sun Jul 06 02:13:03 UTC 2025 - 23.9K bytes - Viewed (0) -
android/guava/src/com/google/common/collect/MapMakerInternalMap.java
Registered: Fri Sep 05 12:43:10 UTC 2025 - Last Modified: Mon Aug 11 19:31:30 UTC 2025 - 90K bytes - Viewed (0) -
android/guava/src/com/google/common/primitives/Ints.java
* in the manner of {@link Number#intValue}. * * <p>Elements are copied from the argument collection as if by {@code collection.toArray()}. * Calling this method is as thread-safe as calling that method. * * @param collection a collection of {@code Number} instances * @return an array containing the same values as {@code collection}, in the same order, converted * to primitivesRegistered: Fri Sep 05 12:43:10 UTC 2025 - Last Modified: Thu Aug 07 16:05:33 UTC 2025 - 31.4K bytes - Viewed (0) -
api/maven-api-plugin/src/main/mdo/plugin.mdo
</field> <field> <name>threadSafe</name> <version>1.0.0/1.1.0</version> <type>boolean</type> <description> Marks this Mojo as being thread-safe, i.e. the Mojo safely supports concurrent execution during parallel builds. Mojos without this annotation will make Maven output a warning when used during a parallel build session.Registered: Sun Sep 07 03:35:12 UTC 2025 - Last Modified: Tue Feb 25 08:28:41 UTC 2025 - 24.8K bytes - Viewed (0) -
src/main/java/org/codelibs/fess/mylasta/action/FessLabels.java
/** The key of the message: Show Login Link */ public static final String LABELS_LOGIN_LINK = "{labels.loginLink}"; /** The key of the message: Thread Name */ public static final String LABELS_THREAD_NAME = "{labels.threadName}"; /** The key of the message: URL */ public static final String LABELS_URL = "{labels.url}";Registered: Thu Sep 04 12:52:25 UTC 2025 - Last Modified: Sat Jul 05 02:36:47 UTC 2025 - 146.4K bytes - Viewed (0) -
src/main/java/org/codelibs/fess/mylasta/action/FessMessages.java
/** The key of the message: Unauthorized request. */ public static final String ERRORS_unauthorized_request = "{errors.unauthorized_request}"; /** The key of the message: Failed to print a thread dump. */ public static final String ERRORS_failed_to_print_thread_dump = "{errors.failed_to_print_thread_dump}"; /** The key of the message: {0} is not supported. */Registered: Thu Sep 04 12:52:25 UTC 2025 - Last Modified: Sat Jul 05 02:36:47 UTC 2025 - 119.6K bytes - Viewed (0)