- Sort Score
- Result 10 results
- Languages All
Results 171 - 180 of 220 for designated (0.19 sec)
-
docs/erasure/README.md
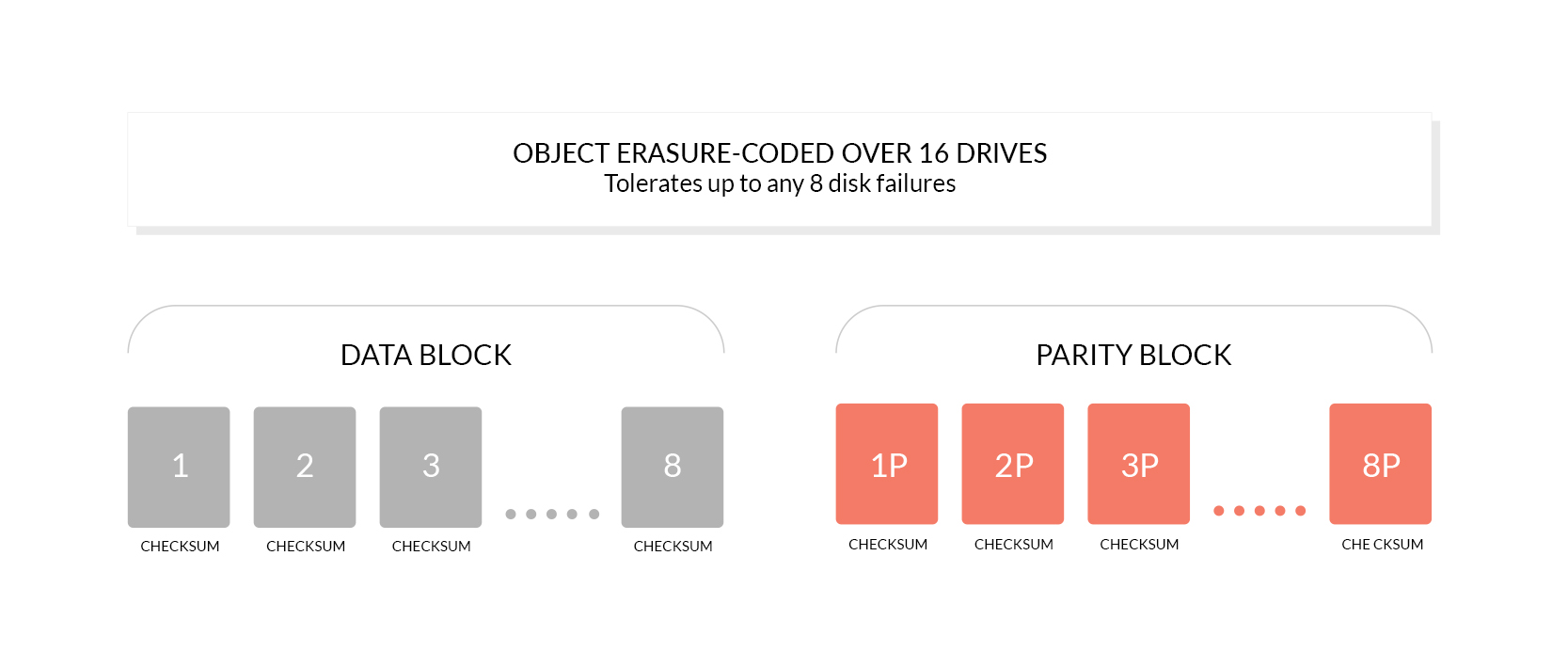 ## What is Bit Rot protection?
Registered: Sun Nov 03 19:28:11 UTC 2024 - Last Modified: Thu Sep 29 04:28:45 UTC 2022 - 4.1K bytes - Viewed (0) -
guava/src/com/google/common/hash/SipHashFunction.java
* or implied. See the License for the specific language governing permissions and limitations under * the License. */ /* * SipHash-c-d was designed by Jean-Philippe Aumasson and Daniel J. Bernstein and is described in * "SipHash: a fast short-input PRF" (available at https://131002.net/siphash/siphash.pdf). */ package com.google.common.hash;
Registered: Fri Nov 01 12:43:10 UTC 2024 - Last Modified: Tue Apr 20 18:43:59 UTC 2021 - 5.3K bytes - Viewed (0) -
common-protos/k8s.io/api/networking/v1alpha1/generated.proto
// At least one of ipv4 and ipv6 must be specified. // This field is immutable. // +optional optional string ipv6 = 4; } // IPAddress represents a single IP of a single IP Family. The object is designed to be used by APIs // that operate on IP addresses. The object is used by the Service core API for allocation of IP addresses. // An IP address can be represented in different formats, to guarantee the uniqueness of the IP,
Registered: Wed Nov 06 22:53:10 UTC 2024 - Last Modified: Mon Mar 11 18:43:24 UTC 2024 - 6K bytes - Viewed (0) -
docs/en/docs/tutorial/security/get-current-user.md
You might remember that request bodies are also declared with Pydantic models. Here **FastAPI** won't get confused because you are using `Depends`. /// /// check The way this dependency system is designed allows us to have different dependencies (different "dependables") that all return a `User` model. We are not restricted to having only one dependency that can return that type of data. /// ## Other models
Registered: Sun Nov 03 07:19:11 UTC 2024 - Last Modified: Sun Oct 06 20:36:54 UTC 2024 - 7.4K bytes - Viewed (0) -
docs/en/docs/tutorial/security/first-steps.md
## The `password` flow Now let's go back a bit and understand what is all that. The `password` "flow" is one of the ways ("flows") defined in OAuth2, to handle security and authentication. OAuth2 was designed so that the backend or API could be independent of the server that authenticates the user. But in this case, the same **FastAPI** application will handle the API and the authentication.
Registered: Sun Nov 03 07:19:11 UTC 2024 - Last Modified: Sun Oct 06 20:36:54 UTC 2024 - 9.2K bytes - Viewed (0) -
SECURITY.md
[XLA](https://www.tensorflow.org/xla) and [JAX](https://jax.readthedocs.io/en/latest/jax-101/02-jitting.html) documentation should be safe, while some of the testing and debugging tools that come with the compiler are not designed to be used with untrusted data and should be used with caution when working with untrusted models. ### Saved graphs and checkpoints When loading untrusted serialized computation graphs (in form of a `GraphDef`,
Registered: Tue Nov 05 12:39:12 UTC 2024 - Last Modified: Wed Oct 16 16:10:43 UTC 2024 - 9.6K bytes - Viewed (0) -
okhttp/src/main/kotlin/okhttp3/RequestBody.kt
* may be sent after response headers or body bytes have been received. * * Though any call may be initiated as a duplex call, only web servers that are specially * designed for this nonstandard interaction will use it. As of 2019-01, the only widely-used * implementation of this pattern is [gRPC][grpc]. * * Because the encoding of interleaved data is not well-defined for HTTP/1, duplex request
Registered: Fri Nov 01 11:42:11 UTC 2024 - Last Modified: Thu Jan 25 14:41:37 UTC 2024 - 9.6K bytes - Viewed (0) -
android/guava/src/com/google/common/hash/Hashing.java
this.hashFunction = new ChecksumHashFunction(this, 32, toString); } } /** * Returns a hash function implementing FarmHash's Fingerprint64, an open-source algorithm. * * <p>This is designed for generating persistent fingerprints of strings. It isn't * cryptographically secure, but it produces a high-quality hash with fewer collisions than some * alternatives we've used in the past. *
Registered: Fri Nov 01 12:43:10 UTC 2024 - Last Modified: Fri Jul 19 16:02:36 UTC 2024 - 29.3K bytes - Viewed (0) -
android/guava/src/com/google/common/collect/GeneralRange.java
import org.checkerframework.checker.nullness.qual.Nullable; /** * A generalized interval on any ordering, for internal use. Supports {@code null}. Unlike {@link * Range}, this allows the use of an arbitrary comparator. This is designed for use in the * implementation of subcollections of sorted collection types. * * <p>Whenever possible, use {@code Range} instead, which is better supported. * * @author Louis Wasserman */Registered: Fri Nov 01 12:43:10 UTC 2024 - Last Modified: Thu Feb 22 21:19:52 UTC 2024 - 10.8K bytes - Viewed (0) -
android/guava-testlib/src/com/google/common/testing/GcFinalization.java
* create the memory pressure required to cause soft references to be cleared. * * <p>This class only provides testing utilities. It is not designed for direct use in production or * for benchmarking. * * @author mike nonemacher * @author Martin Buchholz * @since 11.0 */ @GwtIncompatible @J2ktIncompatible @J2ObjCIncompatible // gc
Registered: Fri Nov 01 12:43:10 UTC 2024 - Last Modified: Sat Oct 19 00:26:48 UTC 2024 - 11.6K bytes - Viewed (0)